 Web Content Viewer
Web Content Viewer
GDPR - General Data Protection Regulation
Whether you are a data controller or a data processor the enactment of the GDPR brings the need for organizations to examine the way data are protected and engage in business process re-engineering to accommodate new and stricter guidelines. This paradigm shift comprises people, processes and technology. From an operations perspective, it can mean business process re-engineering for data handling and storage. It can also mean assigning new roles and responsibilities to employees such as a dedicated data protection officer (DPO) or a data custodian.
Download our GDPR Brochure
At Canon Solutions America we can help our customers who do business with EU organizations by offering them solutions and professional services that can help them to prepare for their GDPR journey as well as remain transparent in their privacy management initiatives. This brochure will give you insight into the following:
- What is the GDPR?
- How it affects US companies
- Privacy Impact Assessment (PIA)
- Security Solutions Portfolio
- And much more!
Re-engineering Business Through People, Process & Technology
PEOPLE
When it comes to data protection, your employees are your first line of defense. But they don't know what they don't know. They may require training to learn how to communicate safely in online venues such as email and the web to help avoid damaging social engineering attacks by malicious actors.
PROCESS
Article 25 (Data Protection by Design and Default) of the GDPR states in part that "the controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organisational measures, such as pseudonymisation1, which are designed to implement data-protection principles, such as data minimisation, in an effective manner and to integrate the necessary safeguards into the processing in order to meet the requirements of this regulation and protect the rights of data subjects."
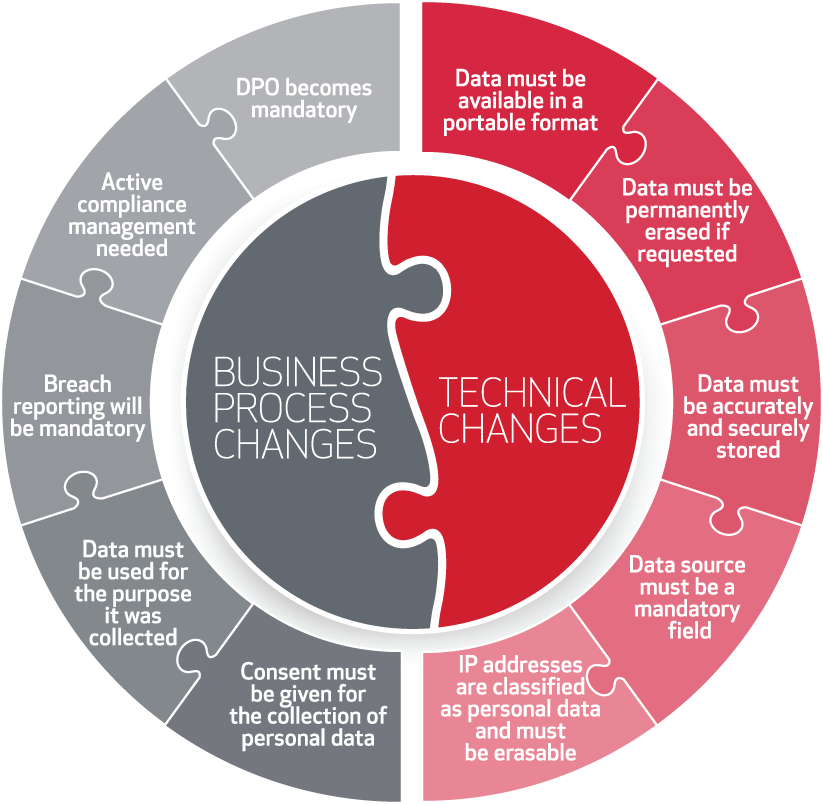
TECHNOLOGY
Article 32 (Security of processing) states in part: "taking into account the state of the art, the costs of implementation, and the nature, scope, context and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons, the controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk."
This can incorporate varying data loss prevention (DLP) technologies to help secure data, not only within the perimeter of an organization, but to also to protect data that travels outside of their domain.
1Pseudonymization is a procedure by which the most identifying fields within a data record are replaced by one or more artificial identifiers, or pseudonyms.
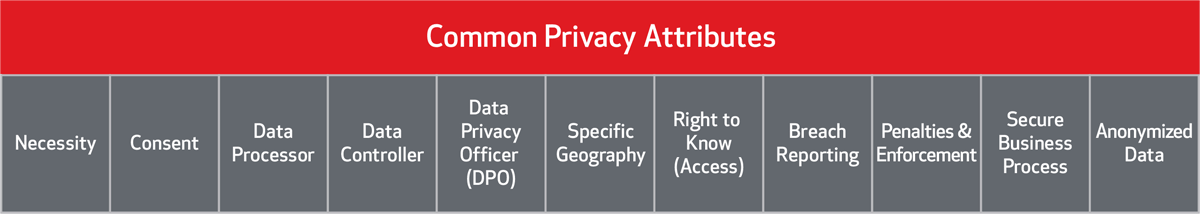
Among the various privacy laws and regulations throughout the world there are some distinct attributes that are common among most of them. This listing can help you to identify areas in your business processes that may need to be modified in order to successfully comply with specific regulations in regions where you do business.
Don't Forget About Third Parties!
Article 4 (7), (8), (9), (10) of the GDPR defines the responsibilities of data controllers and data processors and addresses third parties. As such, the vetting process of a trusted third party and the oversight of such entities' GDPR compliance data processes may fall within your purview. In the event of a data breach while the third party is in possession of protected data, it may render you liable. If you are utilizing third party data processors or for other functions in the supply chain that includes EU data subject information, you are responsible for the consent, confidentiality, and integrity of the data subject's personal information.
Get the Facts from the IAPP
The International Association of Privacy Professionals (IAPP) is a resource for those in the pursuit of helping their organizations successfully manage risk and protecting data. The IAPP is the world’s largest and most comprehensive global information privacy community. Learn what the IAPP knows about the operational impacts of GDPR and what key attributes you need to understand about the privacy imperative that is affecting us all in today’s global business environment. For more information, please visit https://iapp.org/
Explore Solutions and Services That Can Help You Comply
Whether you are a data controller or a data processor, Canon Solutions America maintains one of the largest and most diverse solutions and services portfolios in the U.S.
Click here to find out more


